Recommended method to carry out a secure computation:
- One party modifies a spreadsheet, colouring the input cells of each party: cells which contain inputs from Party A are protected with “Protect Party A”; alternatively, cells which contain inputs from Party B are protected with “Protect Party B”.
- Said party shares the modified spreadsheet file with the other party: both parties must follow the same calculation order with exactly the same formulas, so it’s recommended that the same spreadsheet file is used to prevent errors. The parties input their secret information on their corresponding cells: the cells of the opposite party may contain random inputs, but always respecting the type of the input cell (text inputs must not contain numeric inputs, et vice versa).
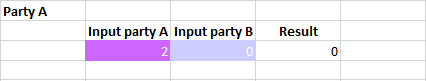
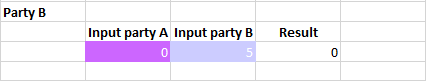
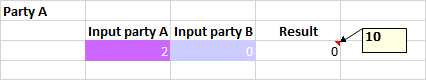
- To start the secure computation, one party chooses a formula cell, then the other party must agree to said initiated secure computation by accepting the received notification or by choosing the same formula cell. The result may appear on a comment, or on an output cell.
NOTES:
- Secure computation is a very demanding task (network and CPU): although all formulas in a non-secure spreadsheet may seem equally complex (eg. a multiplication and a T.INV), their different complexities are clearly revealed when using secure computation. No indication of remaining time until completion can be offered.
- Multiple concurrent secure computations can be executed at the same time: note that there must be only one pending task to be initiated, and until said task is initiated, not other one can be started. Saturating the cores/CPUs or the network may produce unexpected slowdowns.